A possible way to sniff information would be to control an ARP table of a computer. ARP spoofing involves changing the MAC to IP address entries, causing traffic to be redirected from the legitimate system to an unauthorized system of the attacker's choice.
This is achieved by sending out a forged ARP packet to the target system, telling it that its default gateway has changed to the attacker's system. This way, whenever the target system sends traffic on the network, it will send it to the attacker's system first, which then forwards the packet on to its original destination as if nothing ever happened.
| Attack Methods | Let us take a closer look at the attack methodology. There are switches that are not foiled by MAC flooding. These switches stop storing new MAC addresses once their memory reaches a given limit. In this scenario, an attacker can use DSniff's tool called arpspoof. arpspoof allows an attacker to manipulate ARP traffic on a LAN by redefining the ARP table. |
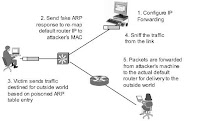
Usually, such attempts are preceded by the scanning and enumeration phases where the attacker draws up a map of the network and discovers the network topology. Looking at the network topology the attacker can decipher the IP address of the default router for the LAN. He then sets up the attack by configuring the IP layer of the attacker's machine to forward any packet it receives from the LAN to the IP address of the default router (IP forwarding). The next step in the attack is sending the fake ARP replies to the victim's machine.
This ARP changes the victims ARP table by remapping the default router's IP (layer 3) to attacker own MAC address (layer2). The victim machine sends the data, forwarding it to what it thinks is the default router (but unknowingly using the attackers MAC address).
The attacker sniffs the information using any kind of sniffing tool. The attacker's machine will promptly forward the victim's traffic to default router on the LAN. Upon reaching the default router the traffic is transmitted to the outside world. The attacker is now sniffing in a switched environment.
- SSL connection uses a session key to encrypt all data sent by server and client.
- SSH is based on the public key encryption idea.
- With SSH a session key is transmitted in an encrypted fashion using a public key stored on the server.
- As such, these protocols - SSL and SSH are sound from a security standpoint. The problem however lies in the basis of these protocols - namely trust certificates and public keys.
One of the precautionary measures advocated to check information leakage by sniffing, is to use a secure protocol. While the S's in HTTPS, SSL and SSH stands for secure, the underlying basis of this is a trust relationship between public keys.
When an HTTPS connection is established, the server sends a certificate which the browser verifies. This certificate is like a digital driver's license identifying the Web server - that, it is indeed who it claims to be. This is endorsed by a certification authority by placing its digital signature on the certificate.
The browser on its part verifies the signature on the certificate to ensure that it is authentic and to verify server's identity. If the certificate was signed by a trusted Certificate Authority, an SSL connection will be established. Now, an SSL connection uses a session key to encrypt all data sent by server and client.
On the other hand, SSH does not support digital certificates though it is based on the public key cryptography. With SSH, a session key is transmitted in an encrypted fashion using a public key stored on the server. As such, these protocols SSL and SSH are sound from a security standpoint. The problem however lies in the basis of these protocols, namely trust certificates and public keys.
For SSL, if a web server sends the browser a certificate and if the browser does not recognize the certificate, it will prompt the user for his consent/approval to accept the certificate. For SSH the user will be warned that server's public key has changed. Nevertheless, he will still be permitted to establish connection to the server, thereby exposing him to attacks. Let us see how dsniff can be used by crackers to exploit this aspect.
No comments:
Post a Comment
Note: Only a member of this blog may post a comment.